How Can We Help?
Elsevier Authentication (Pre 5.30.0)Elsevier Authentication (Pre 5.30.0)
Elsevier ID+ is only supported Elsevier authentication mechanism from 5.30.0
(used only in the Pure hosted edition. Configured by Elsevier)
A common Elsevier Service Provider that participates in various Shibboleth federations provides federated authentication from multiple Elsevier products. Pure supports this authentication mechanism.
This mechanism, although related to SAML2, described below, uses a custom protocol and local WAYF (Where Are You From) implementations where the user can select a federation and institution, before being redirected to their chosen institution’s login screen.
Please note that in order to use this method, the organisation must be a member of a known federation.
To configure Pure to use this mechanism one must perform the following steps:
- Go to Administrator -> security
- Locate "Elsevier Authentication", click Activate
- Configure fields shown in the illustration below.
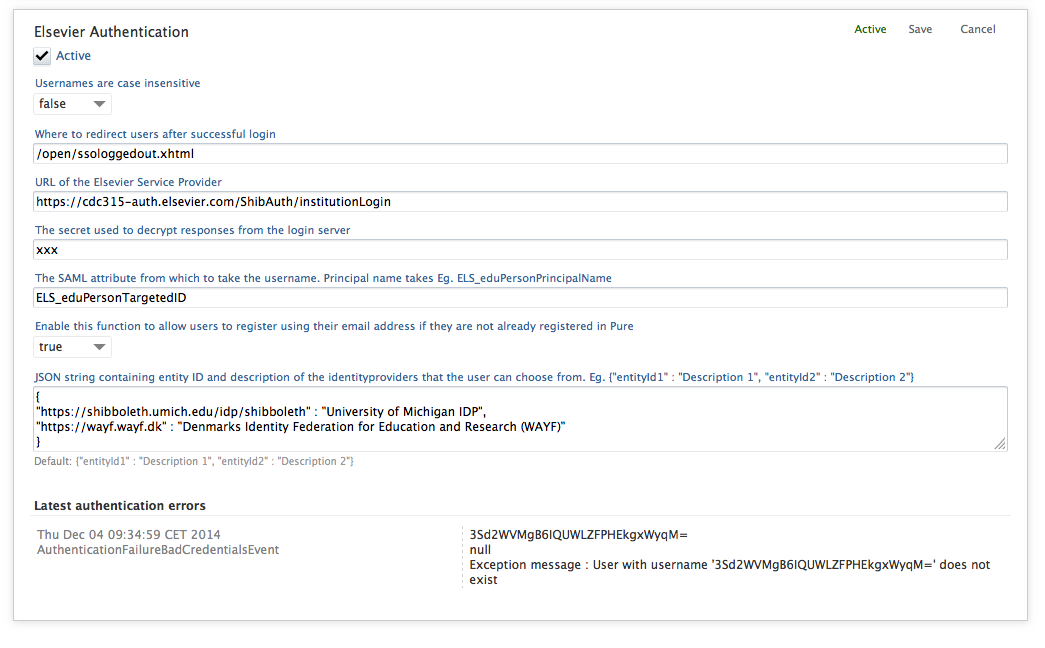
Elsevier Authentication Data Workflow
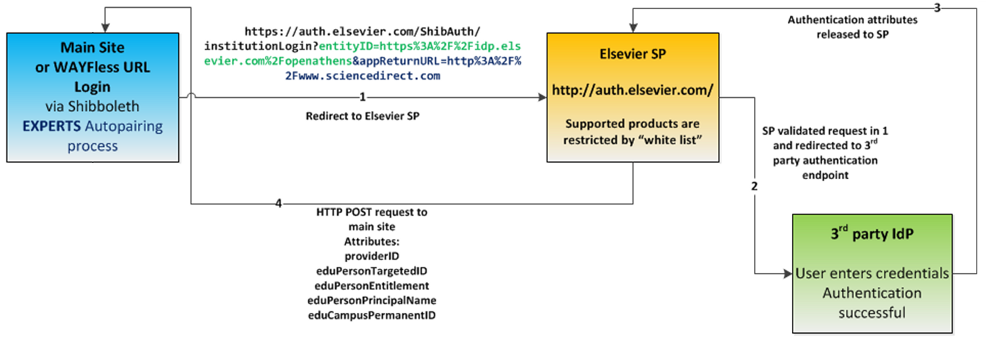
The authentication workflow starts when the user is displayed a list of supported institutions to log in to and chooses one.
- The user request is routed to the Service Provider (SP) with a set of parameters. The SP validates the parameters
entityIDandappReturnUrl, which is a URL that was preconfigured to be accepted by the SP. - Using the
entityIDparameter which is the SAML definition that allows the system know to which Identity Provider (IdP) it must redirect the request, the SP redirects the user to the third party Identity Provider system where she/he is presented with an authentication form. - The user enters the credentials and if the authentication succeeds, it will post a SAML assertion to the SP containing the user attributes and a temporary handle that will identify the browser request with a previously authenticated user.
- The SP creates an HTTP POST request to the application identified by the accepted
appReturnUrl. In this request the SP sends the attributes:target_id,provider_id,entitlement_attributesandshibboleth_attributes. The last one is an encrypted value that contains information such aseduPersonTargetedID,eduPersonEntitlement,edutPersonPrincipalName,eduCampusPermanentID, etc. - Finally, the information contained in the
shibboleth_attributesare evaluated to the expected content. This includes matching the corresponding attribute with information associated with the user attempting to log in. This has to match content from a specified column of the masterlist.
Published at June 27, 2024
