How Can We Help?
Security guideSecurity guide
This guide contains some basic information about how to secure your Pure installation, and some links with more information about how to secure Tomcat.
This guide assumes that you have installed Pure using the Pure installation guide, so you might need to change some of the paths in the examples.
Users
Tomcat should be run as a non privileged user, and it is best if it is run as a user created specifically to only run Tomcat.
Linux
Create user
You should create a new non privileged user and have Tomcat run as that user.
sudo useradd -r -U tomcat |
This will create a system user with no home directory, and also create a group for the user with the same name.
Permissions
First we will change the permission of the Tomcat home directory (/pack/apache-tomcat-<version>) to be owned by root and then make sure that only root is allowed to write to the folders
sudo chown -R root:root /pack/apache-tomcat-8.0.20sudo chmod -R go-w /pack/apache-tomcat-8.0.20 |
We will do the same for the Tomcat base directory (/data/tomcat_base), but here the tomcat user will need write access to some of the sub-folders.
sudo chown -R root:root /data/tomcat_basesudo chown -R tomcat:tomcat /data/tomcat_base/logs /data/tomcat_base/temp /data/tomcat_base/worksudo chmod -R ug+rw /data/tomcat_basesudo chmod -R o-w /data/tomcat_base |
Run Tomcat as user
If you are using the Atira init script, change the following to the user you just created
# Run Tomcat as this userRUN_AS_USER=tomcat |
Windows
Create user
You should create a new non privileged user with Log on as a service rights
Permissions
The new user will need read rights to the following folders including sub-folders:
C:\Program Files\Apache Software Foundation\Tomcat 8.0\- d:\pack\pure_data
And it will also need write rights to these folders including sub-folders:
- d:\pack\pure_data
C:\Program Files\Apache Software Foundation\Tomcat 8.0\logs-
C:\Program Files\Apache Software Foundation\Tomcat 8.0\temp -
C:\Program Files\Apache Software Foundation\Tomcat 8.0\work
Run Tomcat as user
To change what user the Tomcat service runs as, start Tomcat8w.exe from C:\Program Files\Apache Software Foundation\Tomcat 8.0\bin\ and go to the Log On tab.
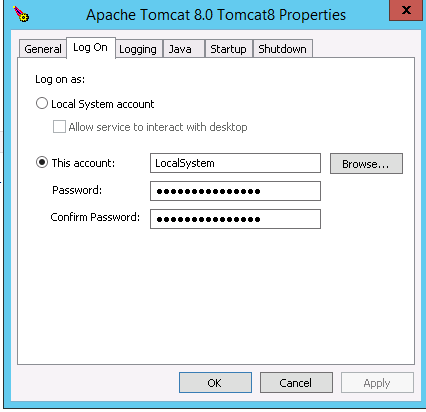
And select This account and input the information for the account you created for Tomcat.
SSL / HTTPS
It is strongly recommended to use HTTPS for all Pure web applications.
It is recommended to use a Proxy in front of Tomcat for this. See Reverse proxy document for some examples.
It can also be set up directly in Tomcat. See the Tomcat SSL/TLS Configuration HOW-TO
Secure cookies
To prevent session sniffing it is recommended that you add the secure attribute to the Tomcat connectors that are used for secure connections.
If you are running everything on your Tomcat through HTTPS, you should just add the secure attribute to the connectors you are using.
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
URIEncoding="UTF-8"
secure="true"
redirectPort="8443" />
...
<!-- Define an AJP 1.3 Connector on port 8009 -->
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443" URIEncoding="UTF-8" secure="true" />If you are running some webapps through HTTPS (eg. admin) and some through HTTP (eg. portal) on the same Tomcat, you will need to add an extra connector to Tomcat, so you have one for HTTPS and one for HTTP, as secure cookies will not work through HTTP.
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000"
URIEncoding="UTF-8"
redirectPort="8443" />
<Connector port="8081" protocol="HTTP/1.1"
connectionTimeout="20000"
URIEncoding="UTF-8"
secure="true"
redirectPort="8443" />
...
<!-- Define an AJP 1.3 Connector on port 8009 -->
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443" URIEncoding="UTF-8" />
<Connector port="8010" protocol="AJP/1.3" redirectPort="8443" URIEncoding="UTF-8" secure="true" />Default Tomcat webapps
If you do not need the default webapps included with Tomcat they should be removed.
For more information see Default web applications in the Tomcat 8 Security Considerations documentation.
Security headers
From version 5.22.0 Pure will set security headers in the application. In particular, the Content-Security-Policy header is generated based on the current configuration of the Pure instance, and is much more specific in what is allowed for which hosts. Here is an example of how the security headers set by the application look like:
Referrer-Policy: origin
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Permissions-Policy: accelerometer=(), camera=(), geolocation=(), gyroscope=(), magnetometer=(), microphone=(), payment=(), usb=()
Content-Security-Policy: default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval' https://js-agent.newrelic.com https://bam.nr-data.net https://www.google-analytics.com https://assets.adobedtm.com https://cdn.pendo.io https://app.pendo.io https://data.pendo.io https://pendo-static-5644800010354688.storage.googleapis.com https://pendo-io-static.storage.googleapis.com; frame-ancestors 'self' https://app.pendo.io; connect-src 'self' https://bam.nr-data.net https://www.google-analytics.com https://smetrics.elsevier.com https://app.pendo.io https://cdn.pendo.io http://metrics.elsevier.com https://data.pendo.io https://dpm.demdex.net https://elsevier.com https://pendo-static-5644800010354688.storage.googleapis.com; img-src 'self' https://smetrics.elsevier.com http://metrics.elsevier.com https://app.pendo.io https://cdn.pendo.io https://pendo-static-5644800010354688.storage.googleapis.com https://data.pendo.io https://cm.everesttech.net https://dpm.demdex.net; frame-src 'self' https://elsevier.demdex.net https://app.pendo.io; style-src 'self' 'unsafe-inline' https://app.pendo.io https://cdn.pendo.io https://pendo-static-5644800010354688.storage.googleapis.com; font-src 'self'; form-action 'self'; object-src 'none'; child-src 'self' https://app.pendo.io;For Pure versions older than 5.22.0 we expect customers to set the relevant security headers themselves in the Apache.
You can set security headers in the Apache configuration for the Pure web applications:
Apache header directives
Header set Referrer-Policy: origin
Header set X-Content-Type-Options: nosniff
Header set X-Frame-Options: SAMEORIGIN
Header set Content-Security-Policy: "default-src 'self' *.elsevier.com cdn.plu.mx api.plu.mx d39af2mgp1pqhg.cloudfront.net ajax.googleapis.com *.pendo.io pendo-static-5644800010354688.storage.googleapis.com pendo-io-static.storage.googleapis.com *.adobedtm.com *.demdex.net cm.everesttech.net *.youtube.com i.ytimg.com *.vimeo.com *.altmetric.com d1bxh8uas1mnw7.cloudfront.net *.googletagmanager.com *.google-analytics.com *.hotjar.com cdn.cookielaw.org maps.googleapis.com www.google.com *.gstatic.com fonts.googleapis.com stats.g.doubleclick.net hcaptcha.com *.hcaptcha.com geolocation.onetrust.com *.onetrust.com 'unsafe-inline' 'unsafe-eval' data:; img-src * data: maps.gstatic.com *.googleapis.com;"These headers have been validated against Pure and Pure portal. Please note that this does not cover custom portals.
For custom portals you can check the used resources by using the report only feature:
Report only directive
Header set Content-Security-Policy-REPORT-Only "default-src 'self' 'unsafe-inline' 'unsafe-eval' data:;"Use the browser web console to view the used resources.
Additional information
You can find additional information about securing Tomcat on the following pages
Published at November 08, 2023
